AWS Best Practices when using RONIN
We recommend all of our customers use the AWS Well Architected Tool to ensure when using RONIN that they adhere to the AWS Well-Architected Five Pillars Framework.

RONIN does a lot of things. But there are still tasks you need to undertake to ensure your cloud account is both secure and functional.
We recommend all of our customers use the AWS Well Architected Tool to ensure when using RONIN that they adhere to the AWS Well-Architected Five Pillars Framework.
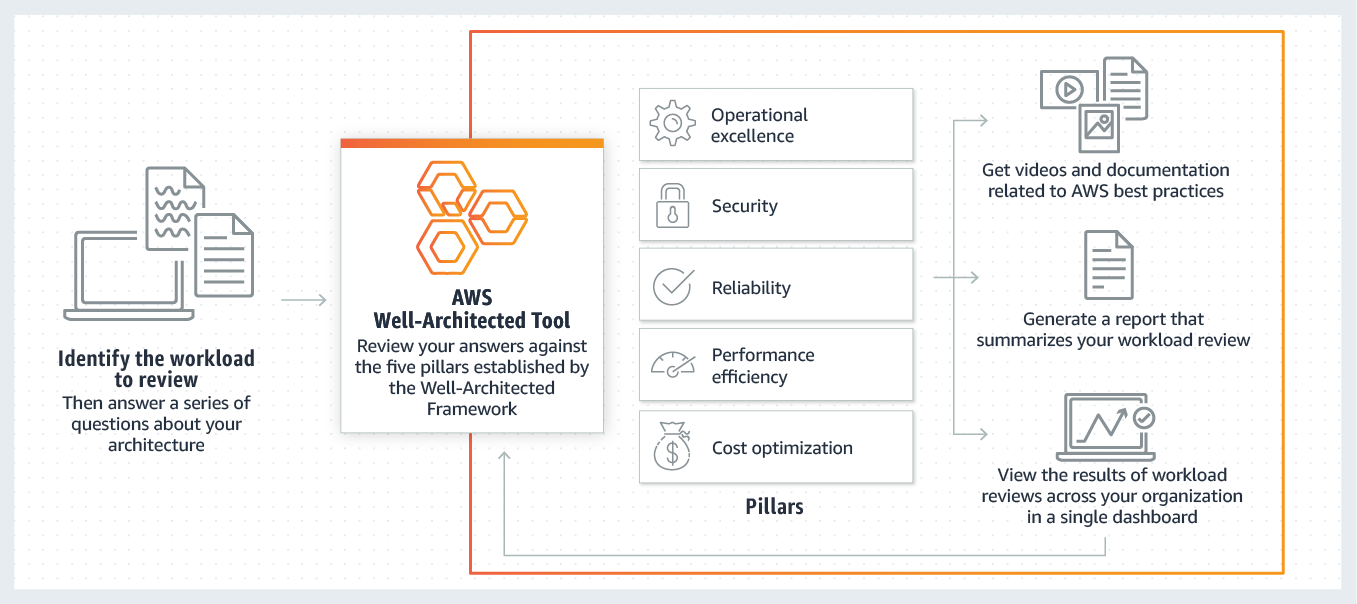
Below are some common recommendations that RONIN customers should undertake and review periodically to ensure a successful experience when using AWS.
Enable additional protection to AWS CloudTrail Logs
AWS CloudTrail log bucket contents must be protected with versioning or MFA-delete or an equivalent solution. To learn more about baseline audit and logging requirements, watch Baseline Bits 03: Audit and Logging on AWS Accounts.
Enable validation of Cloudtrail logs
Validated log files are especially valuable in security and forensic investigations. For example, a validated log file enables you to assert positively that the log file itself has not changed, or that particular user credentials performed specific API activity. The CloudTrail log file integrity validation process also lets you know if a log file has been deleted or changed, or assert positively that no log files were delivered to your account during a given period of time. For more information, see Enabling Validation and Validating Files.
Change / Rotate your IAM keys regularly
You must change your access keys regularly, and make sure that all IAM users in your account do as well. If an access key is compromised without your knowledge, you limit how long the credentials can be used to access your resources. For more information about rotating access keys for IAM users, see Rotating Access Keys. To learn more about baseline IAM configuration requirements, watch Baseline Bits: 03 AWS Root Account Protection and AWS Identity and Access Management Configuration.
Utilise AWS Trusted Advisor to monitor and alert when s3 buckets go public
You must have monitoring or alerting in place to identify when S3 buckets become public. Trusted Advisor checks for S3 buckets that have open access permissions. Bucket permissions that grant List access to everyone can result in higher than expected charges if objects in the bucket are listed by unintended users at a high frequency. Bucket permissions that grant Upload/Delete access to everyone create potential security vulnerabilities by allowing anyone to add, modify, or remove items in a bucket.
Ensure any cross account access has Least Privilege access
The policy created for cross-account access in customer accounts must follow the least privilege principle. The RONIN team can provide a role policy document for customers to use to ensure that the roles created have minimum required privileges.
Use a unique, generated external ID for cross account access
When configuring cross-account access using IAM roles, you must use a value you generate for the external ID, to ensure the integrity of the cross account role configuration. When you generate the ID it ensures that malicious parties cannot impersonate the configuration of another customer and they are able to enforce uniqueness across all of their customers as well as ensure that the external ID format remains at a consistent level. If you are not generating an external ID today we recommend implementing a process that ensures a random unique value, such as a Universally Unique Identifier, is generated for the external ID that a customer would use to setup a cross account role.
Ensure external IDs can't be modified and collection of credentials is disabled
Ensure you have switched to the new method, and collection of credentials should be disabled for new customers. To learn more about baseline cross-account access requirements, watch Baseline Bits 04: Using AWS Identity and Access Management Roles for Cross-Account Access
Follow Trend Micros Best Practice Rules for AWS

Follow these guidelines and your AWS Cloud account will be happy and secure for years to come. Please email us at admin@ronin.cloud if you need any assistance with any of these guidelines.
Now you have Cloud Power Armour!